Tuesday, 21 June 2016
Citrix's GoToMyPc users exposed after password leak
If you are a user of Citrix's GoToMyPC unfortunately you will have to reset your passwords (use something long varied and strong, don't reuse an old password!).
The service, which lets users remotely access PCs over the internet, was hit by a "very sophisticated password attack," Citrix said Sunday in a blog post. The company is requiring users to reset their passwords using the "forgot password" link. This is just another hack in a long line that have been disclosed in the past few weeks as hackers seem to be targeting website with huge user databases in an attempt to reap the rewards of cybercrime.
"Citrix takes the safety and security of its customers very seriously, and is aware of the password attack on GoToMyPC," said John Bennett, product line director at Citrix, in a statement. "Once Citrix learned about the attack, it took immediate action to protect customers. Citrix can confirm the recent incident was a password re-use attack, where attackers used usernames and passwords leaked from other websites to access the accounts of GoToMyPC users. Further, there is no indication of compromise to any other Citrix product line."
To reset your GoToMyPC password, go to the site and click on the Log In link.
I would recommend along with resetting your password that you enable two-step verification, a process that sends a code to your phone each time you want to sign in. If you've used the same password for GoToMyPC at other websites or for other accounts, you should change it at those places as well and don't make up a new password and use it on your other sites to, not that you would do such a thing.
Wednesday, 15 June 2016
Ransomware now targets Smart TV's
And the saga continues...... just when you thought it couldn't get any worse some ass just created a strain of ransomware that can infect Smart Tv's. Lets set the mood, you come home from a stressful day at the office get some dinner and sit down to watch your favorite channel to discover a message demanding bitcoin to gain access to your Tv, now I'm guessing that will put you in great form for the evening. Thanks to a new version of the Frantic Locker (better known as FLocker) Ransomware has now the ability to infect and lock down your Smart TVs until you pay up the ransom making the above scenario much more realistic.
Researchers at Trend Micro have discovered the updated version of FLocker that is capable of locking Android smartphones as well as Smart TVs. Originally launched in May 2015, the FLocker ransomware initially targeted Android smartphones with its developers constantly updating the ransomware and adding support for new Android system changes. So what exactly does Smart Tv locking ransomware do ? is it the same as the other nasty laptop/desktop strains ? Well the answer to those questions is yes and no.
- FLocker locks the device's screen.
- Displays a fake notice from United States Cyber Police or other law enforcement agency, accusing potential victims of crimes they did not commit.
- Demands $200 worth of iTunes gift card as Ransom to unlock the infected TV.
However, if FLocker detects devices outside these countries, the malware
will wait for 30 minutes before requesting admin privileges for the
device. If the victim rejects the request, FLocker freezes the screen,
faking a system update.
"The C&C [command and control] then delivers a new payload misspelled.apk and the ‘ransom’ HTML file with a JavaScript (JS) interface enabled," Trend Micro said. "This HTML page has the ability to initiate the APK installation, take photos of the affected user using the JS interface, and display the photos taken in the ransom page."
"The C&C [command and control] then delivers a new payload misspelled.apk and the ‘ransom’ HTML file with a JavaScript (JS) interface enabled," Trend Micro said. "This HTML page has the ability to initiate the APK installation, take photos of the affected user using the JS interface, and display the photos taken in the ransom page."
Although the new variant of FLocker does not encrypt files on the infected device, it has the capability of stealing data from the device, including contacts, the phone number, device information and location data. Trend Micro's report does not make it clear that how FLocker infects smart TVs, but it does note that typically ransomware infection arrives via SMSes or malicious links.
Therefore, like always you should be wary while browsing the Internet, and receiving text messages or emails from unknown sources. In the event that you do get hit with Flocker there are a number of steps that you can take to get your device back.
How to Remove FLocker from Your Smart TV?
If your Android smart TV gets infected, you should contact the device vendor (phone carrier or TV merchant), or if you are kind of technical, you can remove the ransomware after removing its device admin privileges.
"Users can connect their device with a PC and launch the ADB shell and execute the command 'PM clear %pkg%'," Trend Micro said. "This kills the ransomware process and unlocks the screen. Users can then deactivate the device admin privilege granted to the application and uninstall the app."I would advise however that you contact your vendor first before you go all tech wizard on your Tv. Just incase you get infected by some new strain that may not have been thought up yet as this may signal the start of a new targeting faze in the age of the iot.
Labels:
android,
Cyber security,
FLocker,
hacking,
Ransomware,
recover,
smart TV,
Update
Monday, 6 June 2016
TeamViewer Confirms Hack
For those who are not familiar with the service TeamViewer allows computer professionals and consumers to log into their computers from remote locations. For just over month, a growing number of users have reported their accounts were accessed by cyber criminals who used their highly privileged access and drain PayPal and bank accounts. On Sunday, TeamViewer spokesman Axel Schmidt acknowledged to Ars that the number of takeovers was "significant," but he continued to maintain that the compromises are the result of user passwords that were compromised through a cluster of recently exposed megabreaches involving more than 642 million passwords belonging to users of LinkedIn, MySpace, and other services.
So if you have a TeamViewer account the hackers news have put together the steps that you should take to make sure that you are secure, see below.
Here's What you should do:
TeamViewer users are strongly recommended to change their account passwords and use a strong one, and of course, NOT to use the same credentials across multiple sites.
I know, remembering different passwords for different accounts is a real pain, but you can use a good password manager to solve this issue.
Meanwhile, users should also ensure their TeamViewer accounts are protected with a randomly generated password that is at least 10 characters long, contains numbers, symbols, and uppercase and lowercase letters, and is unique.
It is always a good idea to run the TeamViewer software only when it's truly needed, instead of allowing it to auto-start each time your PC is turned on.
Thursday, 28 April 2016
Decryption tool released for CryptXXX Ransomware
And so the story continues, in the fight against ransomware and cyber-crime Kaspersky labs have yet again come to the rescue with a decryption tool for the CryptXXX ransomware.
Victims of this strain of ransomware should download Kaspersky’s utility (available here), open “Settings,” and choose which drive types they want to have scanned. They should then click “Start scan” and choose where the encrypted .CRYPT file lies.
After asking for where the original file is located, the decryption tool will look for all other files with the .CRYPT extension and will attempt to decrypt those, as well.
I would yet again urge people to educate themselves around how phishing campaigns and dodgy website's are spreading ransomware to end users. I also urge end users to remember that a lot of the more nasty varieties of ransomware have no decryption tool available and there may not be one available for quite some time.
Tuesday, 19 April 2016
Uninstall QuickTime for Windows
If you are a windows user and have the popular quick time application installed on your machine the time has come to part ways and you should uninstall it. The reason for this is the recent disclosure of two zero-day vulnerabilities that have been discovered in the application. The fact that the application contains a zero-day exploits isn't as bad as the fact that apple won't be releasing a patch to fix the vulnerability. This disclosure means that hackers will be actively targeting windows users looking for the quick time application and if you haven't it uninstalled well then you are vulnerable to an attack. Quick Time for Windows follows other software such as Microsoft Windows XP and Oracle Java 6, which are no longer being updated to fix vulnerabilities. That makes them subject to ever-increasing risk as more and more unpatched vulnerabilities are found and cybercriminals attempt to exploit them. The call for users and companies to uninstall Quick Time has been echoed across the security industry so get yourself over to the control panel > add remove programs > Quick Time> Uninstall.
Monday, 11 April 2016
Unlock files infected by Petya Ransomware
As many people are well aware ransomware has spread through the internet like a wild bush fire encrypting millions of machines across the world. The good news if any is that researchers have broken the petya strain of this plague. This mean that if your machine has been encrypted by this particular strain then you are in luck, don't pay any money over to these criminals get a tech savvy friend and do the following. Download this tool created by Leostone that exploits a mistake made by Petya's author in the way that the ransomware encrypts a file on a Windows machine, opening opportunities for the decryption key to be determined. To use the decryption tool you will need to attach the Petya affected drive to another computer and extract specific data from it hence why I said get a tech savvy friend. The data that needs to be extracted is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the petya pay no ransom site to generate the key.
As luck would have it security researcher Fabian Wosar has developed a "Petya Sector Extractor that can collect the specific data needed to use Leostone's tool. All a user needs to do is load up their hard drive on an uninfected Windows computer and run Wosar's solution.
After copying and pasting the information generated by the Petya Sector Extractor, victims can then use Leostone's tool to generate a decryption key. That key will decrypt the victim's infected files once the hard drive has been once again loaded into the infected computer. If you have been infected by other strains of ransomware check out some of my past posts to check if there is a crack available that you can utilize. Until next time all I can say is "think before you click".
Thursday, 31 March 2016
Protect Your PC against CTB-Locker, Locky and TeslaCrypt Ransomware
After dealing with a number of nasty .Locky ransomware cases in the past few weeks I am delighted to announce that Bitdefender has created an anti-ransomware vaccine that blocks the strains CTB-Locker, Locky and TeslaCrypt. This is something that everyone should be downloading ASAP and trust me on this as prevention in this case is much better than paying the fine.
According to data recently published by Fortinet, top ransomware families are CryptoWall, Locky, and TeslaCrypt, while Cryptowall is predominant, Lock is rapidly spreading.
The Bitdefender Anti-Ransomware toolkit was developed by the company years ago to help victims of crypto-ransomware to prevent infections. Some ransomware-decryptors try to exploit encryption flaws in the ransomware implementation to decrypt files or use encryption keys discovered by law enforcement during their activity. These conditions are not easy to match, so Bitdefender is promoting the prevention instead by spreading its anti-ransomware vaccine. So that is enough of me waffling go and download and install the anti- ransomware vaccine HERE.
RANSOMWARE DECRYPTOR:
In the case that you have been hit with ransomware there is still the possibility that you will be able to decrypt the encryption depending on the strain. The National High Tech Crime Unit (NHTCU) of the Netherlands’ police, the Netherlands’ National Prosecutors Office and Kaspersky Lab, have been working together to fight the CoinVault and Bitcryptor ransomware campaigns. In doing so they have released a new decryption application that will automatically decrypt all files for Coinvault and Bitcryptor victims. For more information please see this how-to guide. For TelsaCrypt Cisco have also released a decryption tool however I have not personally used this so I can't comment but if you want to take a look you can find it here.
How to Protect Yourself from Macro-based Malware?
Below is a number of pointer's from The Hacker News on protecting against macro-based malware that may also be of interest.Step 1: Configure Trusted Location
Since disabling Macros is not a feasible option, especially in an office
environment where Macros are designed to simplify the complex task with
automation.
So, if your organization relies on Macros, you can move files that use Macros into the company’s DMZ (Demilitarized Zone), also called Trusted Location.
So, if your organization relies on Macros, you can move files that use Macros into the company’s DMZ (Demilitarized Zone), also called Trusted Location.
To configure the trusted location, you can navigate via:
User Configuration/Administrative Templates/Microsoft Office XXX 20XX/Application Settings/Security/Trust Center/Trusted LocationsOnce configured, the Macros that does not belong to the trusted location would not run in any way, beefing up your system’s security.
Step 2: Block Macros in Office Files that came from the Internet
Microsoft had recently unveiled
a novel method by implementing a new tactical security feature to limit
the Macro execution attack in MS Office 2016, ultimately preventing
your system from hijacking.
The new feature is a group policy setting that lets enterprise administrators to disable macros from running in Office files that come from the Internet.
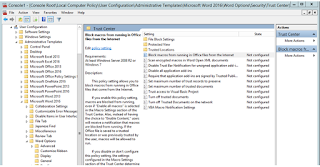
The new setting is called, "Block macros from running in Office files from the Internet" and can be navigated through the group policy management editor under:
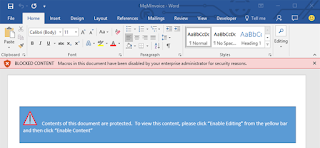
By enabling this option, macros that come from the Internet are blocked from running even if you have 'enable all macros' in the Macros Settings.
Moreover, instead of having the option to 'Enable Editing,' you'll receive a notification that macros are blocked from running, as the document comes from an Untrusted Source.
The only way to run that particular Office file is to save it to a trusted location, allowing macros to run.
The new feature is a group policy setting that lets enterprise administrators to disable macros from running in Office files that come from the Internet.
The new setting is called, "Block macros from running in Office files from the Internet" and can be navigated through the group policy management editor under:
User configuration > Administrative templates > Microsoft Word 2016 > Word Options > Security > Trust CenterIt can be configured for each Office application.
By enabling this option, macros that come from the Internet are blocked from running even if you have 'enable all macros' in the Macros Settings.
Moreover, instead of having the option to 'Enable Editing,' you'll receive a notification that macros are blocked from running, as the document comes from an Untrusted Source.
The only way to run that particular Office file is to save it to a trusted location, allowing macros to run.
Subscribe to:
Posts (Atom)