Showing posts with label Francis Gorman. Show all posts
Showing posts with label Francis Gorman. Show all posts
Tuesday, 25 April 2017
Securely implementing a home network
As we speak I am currently in the process of designing my new home, lucky enough myself and my wife to be are in the position where we get to build from scratch. The beauty with building from scratch is of course you start with a blank canvas. We are at the stage where all the necessities have been figured out such as heating systems, insulation, build type, house size etc so its time to get to the really fun part... the home network.
Having past my CCNA over 3 years ago, my networking has gone a tad off the boil so this is a great excuse to get myself back up to scratch. The beauty with building a network from scratch is you can do whatever you want and that is exactly what I plan on doing. As I do work in security I won't be detailing the underlying hardware components but I will give the high level view.
My first consideration is cable type and at a little more expense I have decided to run with CAT 6A throughout the house, remember if you chose CAT 6A make sure your wall jacks are also CAT 6A and any other network hardware component that delivers connectivity throughout your home.
For flexibility I will be running with un-shielded pair CAT 6A and I am also going to run in some external cable in case I ever decide to run CCTV.
I aim to install approximately 26 ports internally and a number externally so I have chosen a 48 port managed switch to connected everything to.
Choosing your switch is important from a network security and stability perspective you should try get a switch that supports, multiple VLANS, QoS, Access Controls Lists, IP Source Guard, Port-level controls, Dynamic ARP inspection. This will cost a few bob but will give you great control over how your network works. The above are just examples of a few security features and if you want to know more about each I'm sure google will be an obliging teacher.
From a general helpfulness note when you pull in your cables label each one on the wall and give it a corresponding number of the switch. This practice can be a pain in the ass but you will thank yourself later. Once you have your ports labelled and patched its time to decide the function of each port and make a list.
I suggest grouping the ports that will carry the same traffic together such as:
- Wireless Access Point traffic
- VOIP traffic
- IOT devices
- Media and Smart TVs
- Home Heating System / Solar
- CCTV
- Office
Once you have worked out what ports are mapping to what service group these ports into VLANs, this will help protect your traffic by segregating your services and helping to aggregate your network.
For ports where the devices wont change I suggest binding the MAC address to add a small bit of integrity. Switches with QoS options are great as you can now easily configure what traffic you want to give priority to such as VOIP or media. This gives you a more granular control over how your networked devices will work.
I suggest you also buy a switch that has a number of gigabit up-link ports so you can connect into your router.
For my choice of router I want something that is capable of holding a solid baseline and is powerful, I also want it to be able to handle VOIP traffic and run a VPN. Installing a VPN at the router level can cause issues so unless your technical I might skip this part remember I have no problem spending my weekends fluting around with this stuff till its fine tuned.
There is also the option to add in additional security such as firewalls or I could fire up SNORT to give me some intrusion detection capabilities all of which I have ample time to prepare for. The main point of this post is that implementing a home network should cause you to think about how you want it to work, what you want to use it for and how secure you want to be. If your not technical leave it to the pros but make sure you get someone who knows what there doing or you could be exposing yourself to a whole world hurt.
Thursday, 30 June 2016
Find out how much Google knows about you using "My Activity" Dashboard
It is widely understood that Google as a company holds masses of information on the majority of us. If you have ever wanted to know just how much information Google knows about you this is now possible. Google tracks the majority of what you do on the Internet, including your searches, music you listen to, videos you watch, and even the places you travel to, and it does this for targeting relevant ads to its users and better improve its service. Now the technology giant has a plan to make it easier to control all the data the company collects throughout all your different devices.
So how are Google going to make this information easier for you to access and control? The answer to this is through the roll out of there new "My Activity" page that shows a searchable history of pretty much everything you do online, including previously visited websites, voice searches, searched things and places, watched Netflix programs, and all activities you did on each of its products. These activities are sorted by most recent and broken down into individual items some items may be part of groups that bundle similar activities together. You can log into this page here.
The feature along with been terrifying is beneficial for those who want more granular control over how ads work across all their devices linked with Google account and gives them the ability to block some ads they don't want to see. However, thankfully the feature also offers you an option to delete items as well — everything in a particular date range or by specific topics.
If you are privacy conscious, you can adjust your settings in the Privacy Checkup. You can change your settings for ultimate privacy, depending on how much of your online activity you allow Google to track. I would recommend that you do this but if you like targeted adds and a super computer giant knowing everything you do online, well then don't change a thing.
Tuesday, 21 June 2016
Citrix's GoToMyPc users exposed after password leak
If you are a user of Citrix's GoToMyPC unfortunately you will have to reset your passwords (use something long varied and strong, don't reuse an old password!).
The service, which lets users remotely access PCs over the internet, was hit by a "very sophisticated password attack," Citrix said Sunday in a blog post. The company is requiring users to reset their passwords using the "forgot password" link. This is just another hack in a long line that have been disclosed in the past few weeks as hackers seem to be targeting website with huge user databases in an attempt to reap the rewards of cybercrime.
"Citrix takes the safety and security of its customers very seriously, and is aware of the password attack on GoToMyPC," said John Bennett, product line director at Citrix, in a statement. "Once Citrix learned about the attack, it took immediate action to protect customers. Citrix can confirm the recent incident was a password re-use attack, where attackers used usernames and passwords leaked from other websites to access the accounts of GoToMyPC users. Further, there is no indication of compromise to any other Citrix product line."
To reset your GoToMyPC password, go to the site and click on the Log In link.
I would recommend along with resetting your password that you enable two-step verification, a process that sends a code to your phone each time you want to sign in. If you've used the same password for GoToMyPC at other websites or for other accounts, you should change it at those places as well and don't make up a new password and use it on your other sites to, not that you would do such a thing.
Thursday, 28 April 2016
Decryption tool released for CryptXXX Ransomware
And so the story continues, in the fight against ransomware and cyber-crime Kaspersky labs have yet again come to the rescue with a decryption tool for the CryptXXX ransomware.
Victims of this strain of ransomware should download Kaspersky’s utility (available here), open “Settings,” and choose which drive types they want to have scanned. They should then click “Start scan” and choose where the encrypted .CRYPT file lies.
After asking for where the original file is located, the decryption tool will look for all other files with the .CRYPT extension and will attempt to decrypt those, as well.
I would yet again urge people to educate themselves around how phishing campaigns and dodgy website's are spreading ransomware to end users. I also urge end users to remember that a lot of the more nasty varieties of ransomware have no decryption tool available and there may not be one available for quite some time.
Thursday, 31 March 2016
Protect Your PC against CTB-Locker, Locky and TeslaCrypt Ransomware
After dealing with a number of nasty .Locky ransomware cases in the past few weeks I am delighted to announce that Bitdefender has created an anti-ransomware vaccine that blocks the strains CTB-Locker, Locky and TeslaCrypt. This is something that everyone should be downloading ASAP and trust me on this as prevention in this case is much better than paying the fine.
According to data recently published by Fortinet, top ransomware families are CryptoWall, Locky, and TeslaCrypt, while Cryptowall is predominant, Lock is rapidly spreading.
The Bitdefender Anti-Ransomware toolkit was developed by the company years ago to help victims of crypto-ransomware to prevent infections. Some ransomware-decryptors try to exploit encryption flaws in the ransomware implementation to decrypt files or use encryption keys discovered by law enforcement during their activity. These conditions are not easy to match, so Bitdefender is promoting the prevention instead by spreading its anti-ransomware vaccine. So that is enough of me waffling go and download and install the anti- ransomware vaccine HERE.
RANSOMWARE DECRYPTOR:
In the case that you have been hit with ransomware there is still the possibility that you will be able to decrypt the encryption depending on the strain. The National High Tech Crime Unit (NHTCU) of the Netherlands’ police, the Netherlands’ National Prosecutors Office and Kaspersky Lab, have been working together to fight the CoinVault and Bitcryptor ransomware campaigns. In doing so they have released a new decryption application that will automatically decrypt all files for Coinvault and Bitcryptor victims. For more information please see this how-to guide. For TelsaCrypt Cisco have also released a decryption tool however I have not personally used this so I can't comment but if you want to take a look you can find it here.
How to Protect Yourself from Macro-based Malware?
Below is a number of pointer's from The Hacker News on protecting against macro-based malware that may also be of interest.Step 1: Configure Trusted Location
Since disabling Macros is not a feasible option, especially in an office
environment where Macros are designed to simplify the complex task with
automation.
So, if your organization relies on Macros, you can move files that use Macros into the company’s DMZ (Demilitarized Zone), also called Trusted Location.
So, if your organization relies on Macros, you can move files that use Macros into the company’s DMZ (Demilitarized Zone), also called Trusted Location.
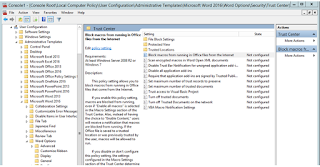
To configure the trusted location, you can navigate via:
User Configuration/Administrative Templates/Microsoft Office XXX 20XX/Application Settings/Security/Trust Center/Trusted LocationsOnce configured, the Macros that does not belong to the trusted location would not run in any way, beefing up your system’s security.
Step 2: Block Macros in Office Files that came from the Internet
Microsoft had recently unveiled
a novel method by implementing a new tactical security feature to limit
the Macro execution attack in MS Office 2016, ultimately preventing
your system from hijacking.
The new feature is a group policy setting that lets enterprise administrators to disable macros from running in Office files that come from the Internet.
The new setting is called, "Block macros from running in Office files from the Internet" and can be navigated through the group policy management editor under:
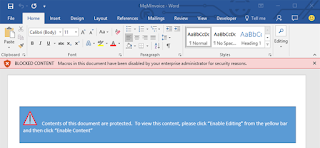
By enabling this option, macros that come from the Internet are blocked from running even if you have 'enable all macros' in the Macros Settings.
Moreover, instead of having the option to 'Enable Editing,' you'll receive a notification that macros are blocked from running, as the document comes from an Untrusted Source.
The only way to run that particular Office file is to save it to a trusted location, allowing macros to run.
The new feature is a group policy setting that lets enterprise administrators to disable macros from running in Office files that come from the Internet.
The new setting is called, "Block macros from running in Office files from the Internet" and can be navigated through the group policy management editor under:
User configuration > Administrative templates > Microsoft Word 2016 > Word Options > Security > Trust CenterIt can be configured for each Office application.
By enabling this option, macros that come from the Internet are blocked from running even if you have 'enable all macros' in the Macros Settings.
Moreover, instead of having the option to 'Enable Editing,' you'll receive a notification that macros are blocked from running, as the document comes from an Untrusted Source.
The only way to run that particular Office file is to save it to a trusted location, allowing macros to run.
Wednesday, 30 March 2016
Disable that annoying Windows 10 Update Forever!
For the past few month's Microsoft have been on a mission to put there new Windows 10 operating system onto every machine in the world. Now this is great if you actually want the new Windows 10 OS but if you don't well then the constant pop up stating "Your FREE Windows 10 upgrade is ready!" may be driving you crazy. Lucky for anyone who doesn't want to update a one click solution has now come to light saving non Windows 10 inclined users all over the world.
A new free tool, dubbed Never10, provides the user a one-click solution to disable Windows 10 upgrade until the user explicitly gives permission to install Windows 10.
Never10 has been developed by Steve Gibson, the well-known software
developer and founder of Gibson Research, which is why the tool is also
known as "Gibson's Never10."
So lets do this, if your ready to disable that update do the following:
- Go to Gibson's Never10 official site and click on the Download.
- Once downloaded, the program detects if the upgrade to Windows 10 is enabled or disabled on your system and then shows a pop-up. If enabled, Click 'Disable Win10 Upgrade' button.
- You’ll again see a pop-up that now shows Windows 10 upgrade is disabled on your system, with two buttons to 'Enable Win10 Upgrade' and 'Exit.' Click on Exit button.
The best part of this tool is that you don't have to install an
application on your PC to do this. Gibson’s Never 10 is an executable.
So you just need to run it, and it doesn’t install anything on your
computer. You can delete it when you're done.
For more technical details on how this tool works, you can head on to this link.
Thursday, 17 March 2016
Prepare Against Ransomware
In recent months you may have come across articles depicting the chaos that ransomware is causing to businesses and individuals alike across the globe. You may ask what is ransomware? In short it is a malicious software that encrypts your computer system so you are unable to access your data. The reason for this is that the distributor of this software is a criminal and they want you to pay them a fee to release your files. Now the fact that they are a criminal you should not pay but in some cases such as hospitals and other critical services where not paying may have a worse knock on effect then sometimes business and individuals are left with little choice but to cough up the dough. In recent month's however a number of companies and state bodies have started to crack different strains of ransomware and release the keys so if you get infected have a look to see if your key is out there you might get lucky. For the rest of you I have compiled a list if useful precautions to take.
Backup regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
Don’t enable macros in document attachments received via email. Many ransomware attacks arrive in documents, and rely on persuading you to enable macros (embedded document scripts). Don’t do it: Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure.
Consider installing the Microsoft Office viewers. These viewer applications let you see what documents look like without opening them in Word or Excel itself. In particular, the viewer software doesn’t support macros at all, so you can’t enable macros by mistake!
Be cautious about unsolicited attachments. Crooks who send malware in documents are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
Don’t give yourself more login power than you need. Most importantly, don’t stay logged in as an administrator any longer than is strictly necessary, and avoid browsing, opening documents or other “regular work” activities while you have administrator rights.
Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit.
UPDATE:
In the past week I came across a case of the .Locky strain of ransomware which seems to be particularly nasty. In researching this strain I came across the below article and it is very much worth a read. You can find the original article here.
-------------------------------------------------------------------------------------------------------------------------
How Just Opening an MS Word Doc Can Hijack Every File On Your System
If you receive a mail masquerading as a company's invoice and containing a Microsoft Word file, think twice before clicking on it.
Doing so could cripple your system and could lead to a catastrophic destruction.
Hackers are believed to be carrying out social engineering hoaxes by adopting eye-catching subjects in the spam emails and compromised websites to lure the victims into installing a deadly ransomware, dubbed "Locky," into their systems.
So if you find .locky extension files on your network shares, Congratulations! You are infected and left with just two solutions: Rebuild your PC from scratch or Pay the ransom.
Locky ransomware is spreading at the rate of 4000 new infections per hour, which means approximately 100,000 new infections per day.
Microsoft MACROS are Back
It is hard to digest the fact that, in this 2016, even a single MS Word document could compromise your system by enabling 'Macros.'
This is where the point to appreciate hacker's sheer brilliance of tactics.

Locky ransomware is being distributed via Microsoft 365 or Outlook in the form of an Invoice email attachment (Word File that embeds vicious macro functions).
The concept of macros dates back to 1990s. You must be familiar with this message: "Warning: This document contains macros."
Now macros are back, as cyber criminals discover a new way to get internet users to open Microsoft Office documents, especially Word files that allow macros to run automatically.
How Does Locky Work?
 Once
a user opens a malicious Word document, the doc file gets downloaded to
its system. However, danger comes in when the user opens the file and
found the content scrambled and a popup that states "enable macros".
Once
a user opens a malicious Word document, the doc file gets downloaded to
its system. However, danger comes in when the user opens the file and
found the content scrambled and a popup that states "enable macros".Here comes the bad part:
- Once the victim enables the macro (malicious), he/she would download an executable from a remote server and run it.
- This executable is nothing but the Locky Ransomware that, when started, will begin to encrypt all the files on your computer as well as network.
Once encrypted, the ransomware malware displays a message that instructs infected victims to download TOR and visit the attacker's website for further instructions and payments.
Locky ransomware asks victims to pay between 0.5 and 2 Bitcoins ($208 to $800) in order to get the decryption key.
One of the interesting note on Locky is that it is being translated into many languages, which heighten its attack beyond English boundaries to maximize the digital casualties.
Locky Encrypts Even Your Network-Based Backup Files
The new ransomware also has the capability to encrypt your network-based backup files. So it's time for you to keep you sensitive and important files in a third party storage as a backup plan in order to evade future-ransomware infections.
A researcher named Kevin Beaumont along with Larry Abrahms of BleepingComputer initiallydiscovered the existence of Locky encrypted virus.
To check the impact of Locky, Kevin successfully intercepted the Locky traffic yesterday and realized that the cryptovirus is spreading out rapidly in the wild.
"I estimate by the end of the day well over 100,000 new endpoints will be infected with Locky, making this a genuine major cybersecurity incident — 3 days in, approximately a quarter of Million PCs will be infected," Kevin said in a blog post.
One hour of infection Statistics:

Among the highly impacted countries include Germany, Netherlands, United States, Croatia, Mali, Saudi Arabia, Mexico, Poland, Argentina and Serbia
Wednesday, 2 March 2016
What is a DROWN attack?
If you have been online in the past few day's chances are that you have seen the headline "new vulnerability discovered in OpenSSL" or something along those lines. This new vulnerability has been dubbed as DROWN (Decrypting RSA with Obsolete and Weakened eNcryption), and it is said to effect over 11 million websites and email services worldwide.
DROWN is a cross-protocol attack that uses weaknesses in the SSLv2
implementation against transport layer security (TLS), and that can "decrypt passively collected TLS sessions from up-to-date clients." While latest versions don't allow SSLv2 connections by default,
administrators sometimes, unintentionally override those settings in an
attempt to optimize applications and this is where the problem lies. The DROWN attack could allow an attacker to
decrypt HTTPS connections by sending specially crafted malicious packets
to a server or if the certificate is shared on another server,
potentially performing a successful Man-in-the-Middle (MitM) attack. It has been reported that more than 33% of all HTTPS servers are vulnerable to DROWN based MITM attacks.
If you want to see if your website is vulnerable to this critical security hole you can check out https://drownattack.com/. If your website is vulnerable there is good news in the fact that an academic
researchers uncovered the DROWN security hole and a patch for the
vulnerability has already been made available with an OpenSSL update. And just in case you get to happy the Bad news is that the DROWN attack
can be conducted in just under a minute and now that the bug has been
disclosed, it may be actively used by hackers to attack servers. So really this isnt something that you want to be putting on the long finger, OpenSSL 1.0.2 users are strongly advised to upgrade to OpenSSL 1.0.2g and OpenSSL 1.0.1 users are recommended to upgrade to OpenSSL 1.0.1s. And if you are using another version of OpenSSL for security, you should move up to the newer versions 1.0.2g or 1.0.1s.
In order to protect yourself against the DROWN attack, you should ensure SSLv2 is disabled, as well as make sure that the private key isn’t shared across any other servers. Those already vulnerable to DROWN attack do not need to re-issue certificates but are recommended to take action in order to prevent the attack immediately. And remember the fact that this has been widely publicized you can be sure that hackers are actively targeting websites that have not implemented the above so get your IT team moving.
Labels:
attack,
Cyber security,
decrypt,
DROWN,
Francis Gorman,
HTTPS,
OpenSSL,
ssl,
TLS
Wednesday, 24 February 2016
Is Facebook tracking me?
Have you logged onto Facebook in the past few months and been targeted with an advert relating to something you recently looked up on your device? For the majority of people the answer to this will be yes. Only a few days ago I searched for the new Jaguar using safari on my iPhone, that evening when I opened the Facebook app I was met with an advert for the new Jaguar XF. This was a very strategically placed targeted advert, and you need to remember that the reason Facebook is free is because we the users are the product. It was reported in the states that Facebook makes approx $7 a year for each and every user by giving marketers access to a defined market based on search history and social patterns of users. Now I have no issue with this, my issue however is I was carrying out searches for the above Jaguar car on safari and not through the Facebook app and this is where it gets a little scary. If I did not use the Facebook app to carry out a search how did I get an advert targeting me for this item? Well my guess is that Facebook is actually monitoring my activity on my phone even though I have it pretty well shutdown. You will notice on all of these adverts that at the top right hand corner there is a little arrow when you click this you get a drop down menu. On this drop down menu you will see the option "why am I seeing this?" This is Facebook's way of telling you why you have been targeted with a specific advert when I clicked on this I got the below information.
As you can see it specifically notes that this information is based on information from your profile and here is the important part AND YOUR DEVICE! Now you can limit Facebook right down by enabling all of your privacy setting but there is no option to click that says "stop spying on my applications outside of Facebook". The issue is if I have limited all of my privacy setting to the highest level how is this information still been obtained? And what information is Facebook gathering from my device? We know that tracking cookies are more than lightly the reason that Facebook can obtain this information so there is one way to stop this, you could stop your device from receiving cookies. This however is not a great solution as you need cookies enabled in order to log into any site where you may have a user account otherwise your session won't run so you can see where the issue lies if you were to turn them off. This means that until someone comes up with an iron clad way to stop tracking cookies from monitoring your online activity it's up to you how much information you really want to share.
Monday, 15 February 2016
5 golden rules for staying safe online
If you have been reading my posts you will notice that a number of points keep popping up. The reason for this is of course that these particular points are vital to keeping yourself safe online. For the few out there who want to do the minimum in order to stay safe I am laying out 5 golden rules to follow.
1) Keep your software updated
2) STOP using the same password everywhere
You are living in an age of big hacks and data breaches if you use the same password everywhere once your details are stolen once all your accounts are compromised. And you can be guaranteed that there is a high possibility your details have already been stolen from somewhere.
3) Don't fall for phishing scams
These scams are getting more and more frequent and the attacks been used are becoming more professional. I recently received an email claiming to be a free password security tester, the email asked me to enter my password to test how strong it is and of course I deleted it as its purpose was of course to steal my password. Be smart when you receive phone calls and emails that you are not expecting and never open an application you receive in an email with the file extension .exe.
4) Add recovery contact information to your accounts
This is important you should always have two different contact methods on your accounts. The reason for this is if you forget your password and lose your phone well then your snookered and you may be locked out of that account forever, leaving your information hanging in cyber space. The second reason for this is If your account is compromised, companies will probably try to let you know. But that’s only possible if they have some means of getting in touch with you on file.
5) Enable two factor authentication
Thursday, 11 February 2016
Protecting your child online
This is the second post I have done on this topic and the reason for this is the increasing amount of questioning that I have been getting from parents around this area. I think in the past year the message is starting to sink in that real threats do occur online and you need to be aware of how to mitigate against them. First of all can I say that educating your child on how to use a computer can be very beneficial but use this time wisely educate your child how to master IT skills through the likes of your local coder dojo or local computer classes for children, I would not however suggest letting your child have unlimited access to your ipad or family computer. In many cases, kids are more technologically advanced than adults, so some parents may feel intimidated and refrain from enforcing rules that are imperative to protect their children as they surf and socialize online. This is a very real fact there are however ways for parents to educate themselves so they can take a more interactive role in how they deal with there children's use of online forums. Security software is one way to restrict what kids see and do on the web, taking a lot of pressure off parents to stay current with every new risk. But it’s still important that parents get involved with their kids’ online lives, and make sure that their children know how to act and how to react to what they see on the web. Communicating the dangers of the web to your child and staying involved in what they can and cannot do online helps build up an understanding of what is safe and acceptable.
In order to communicate these dangers parents firstly need to understand what the potential threats may be. The number one threat to children today be meeting a predator online, but there are many other online experiences that can result in inappropriate or illegal activity. Kids need to be told that not everything they read online is true, and that there is a lot of material on the web that is not meant for them. This material can include fascist sites, pornography sites, drug sites, and other explicit content that an unprotected child can easily view. To help mitigate these risks there are many new software options available such as filtering technologies, child-safe browsers and search engines that restrict where your child can surf.
Loss of privacy is a another big risk. Kids must be shown how important it is to protect their personal information and the information of their family and friends. Many child-oriented web sites solicit information from kids in surveys and forms in exchange for prizes, and get them to register online for fan clubs. In chat rooms, sharing their gender, age, and favorite hangout could seem harmless, but predators can easily use this information to track down the child. Parents need to be aware that digital predators often pose as children in order to gather information and ultimately meet their unsuspecting victims. But kids also flirt and pretend to be older than they actually are, not thinking about the potential results of such actions. It is also common for kids to get into online fights or become the target of bullying via email, chat, and instant messaging, this type of behavior can sometime consume the victim so much that they become withdrawn and with no physical marks to show from such behavior it can become hard for parents to figure out whats going on. With the introduction of such apps like snapchat where the messages disappear from the victims phone within seconds it can be very hard for a child to prove that the bullying exists. I would strongly recommend that parents are very aware of what messaging apps your child is using and carefully monitor there activity especially if the child's behavior starts to change.
Blogs such as this one and Social networking sites such as Facebook are places where kids can share too much information—not only names and addresses but also personal photos that sometimes show illegal acts, such as underage drinking or drug use. Ask your kids to share their blogs or online profiles with you so you can check the content. If you are spicious that your kids are hiding content from you then use Google, along with the search tools on social networking sites, to search for profiles your child may have posted. Use your child’s full name, phone number, and other identifying information. You can also use Google images to upload a picture they may use on social media sites and this will trawl the web for that pictures or ones that may be similar.
So how do parents go about becoming proactive about the above? I have complied a list of ten things that you should sit down with your children and go through. The below list will set out clear boundaries for your child and let them know that you care and are taking a proactive role about there online security.
1) Monitor your child's online activity this is by far the most important step to take. Limit the chance that they are looking up inappropriate material by putting the computer in a high-traffic family area and limit there usage. There are loads of child monitoring software packages out there so do your own research to find a software that meets your needs and budget.
2) Fortify your computer with strong security software and make sure to keep it up to date I have wrote about the importance of this in past blogs so take a look through my posts if you need help with this. Using software such as The McAfee® Internet Security Suite guarantees protection from viruses, hackers, and spyware. It filters offensive content, pictures, and web sites. The anti-virus software will also protect your computer from viruses and spyware by automatically scanning email attachments and files downloaded from P2P file-sharing sites. For the most complete way to keep your children safe online, use McAfee Family Protection. It keeps children of all ages safe from exposure to inappropriate content, social networking risks, strangers, and other online threats. With McAfee, kids are free to safely explore, learn, and enjoy their online interests.
3) Make sure kids understand basic rules for using social networking sites such as Facebook and blogs. They should guard their passwords, and never post personally identifying information or inappropriate photos. Blogs and social networking sites offer privacy tools that can be turned on to restrict potentially dangerous users. The sites automatically provide these protective tools to kids under 15. Kids should share information only with people they know from the real world. Make sure that your kids understand that there are bad people online to and they may not be who they claims its very easy make up a fake social media account.
4) Never ever let your child arrange in-person meetings with people they meet online. If however for some reason you think that this is acceptable you should confirm the person’s identity, and you should accompany your child to the meeting in a public place.
5) When using P2P file-sharing programs, kids should not download files from users whom they don’t know. They could be downloading infected files, pictures, games, and music that are inappropriate, or media files protected by copyright law. As I said above using a virtual machine for this activity will save your computer if they do download a virus. Also its important to note that kids should not allow users to upload their music files unless they’re certain that they have permission to share them. You can disable the upload feature so that your kids don't inadvertently share files without permission.
6) Don’t allow kids to fill out online forms or surveys. If there is a legitimate site where they want to register, such as Nickelodeon or Disney, have them come to you first so you can check the site’s privacy policy and rules of conduct. You should take the time to read there privacy statement but I suggest use a throw away email address for such sign ups and limit the amount of factual information you need to share.
7) Only allow your children to use monitored chat rooms, and have them use a screen name that doesn’t hint at their true identity. As with blogs and MySpace, kids should never reveal personal information or share photos. Make sure they understand that people can lie about who they are and that online friends are still strangers.
8) Teach your kids to ignore emails and instant messages from people they don’t know. They should never open attachments they are not expecting nor click on links in messages. As with blogs and Facebook, they should not send out personal information.
9) Use browsers for kids and kid-oriented search engines. Children’s browsers such as Google safe search for kids do not display inappropriate words or images. It comes pre-loaded with kid-safe web sites and pre-set word filters.
10) Set you kids goals to research online safety be themselves as them to write you a little report on what they think the dangers online might be. Fact Monster is an excellent reference site, packed with information and homework help. For Ireland you should check out the office for internet safety.
How safe are messaging apps
Well in order to help you with this I have compiled a number of steps that if followed should help minimize your risk of exposure if your account becomes victim to a cyber attack.
1) Be discreet. If you want to use messaging apps as a way to contact certain people, avoid using real-life identification details that can be traced back to you. If that can’t be avoided, use as little real information as possible, depending on the app you’re using. Avoid linking your social networking profiles to your messaging app accounts.
2) Secure your messaging app accounts. Use a unique email account for your messaging app. Don’t reuse passwords.
3) Don’t share anything you wouldn’t want the public to get wind of. Oversharing is one of the biggest mistakes you can ever make online; using messaging apps is no exception. Be aware of what you share. And when in doubt, keep sensitive information to yourself.
4) Limit what access you give your messaging application eg don't give access to your location or photos unless you need to.
Tuesday, 9 February 2016
Recovering "Deleted" snapchat messages
You have just arrived at this post and read the heading "recovering deleted snapchat messages" and now your thinking snapchat deletes my messages after 10 seconds doesn't it? Well the simple answer to that question is no. This isn't any kind of a new revelation the research has been around since 2013 it just doesn't seem to be well known so I have decided to do my part to try and highlight it. The main reason for writing this post is to try and get the message through to teenagers and young adults that the content you are sending may not be secure and could come back to bite you. There is also a massive legal issue with the sending of explicit images if both parties are seen as minors and you could land yourself in a whole lot of trouble with the law. It is important to presume that anything you send or do online can be traced and made public so the safest approach to take is think twice before sending anything out there that may prove harmful to yourself or others.
If you would like to read through the report on how to recover snapchat messages and I suggest that you do the link can be accessed here. After reading this report maybe you might consider sending a snap to your friends just to let them know you have a code red situation and you need to meet up. For anyone who is to lazy to click on the link I have copied in the body of the report below.
-------------------------------------------------------------------------------------------------------------------------
Methodology
We used two android devices to examine artifacts left behind by Snapchat. An account (rhickman1989) was created on a Samsung Galaxy Note 2, and pictures and videos were sent to another account (DeciphForensics). The receiving account was logged into on a Samsung Galaxy S3, when some of the images and videos were viewed, while others were not. We then acquired the phone using AccessData’s Mobile Phone Examiner+ version 5.2.1.499. After the acquisition was complete, the image was exported as an .AD1 image file, and then imported to AccessData’s Forensic Toolkit version 4.0.2.33.
After a brief examination of the contents, a different account (decipforensics2) was created on the Samsung Galaxy Note 2, and more pictures and videos were sent to the account on the Samsung Galaxy S3 (rhickman1989). This was to determine if there are identifiers for the sender account of a “snap.” The same acquisition process was followed again after the second batch of “snaps” were sent.
After another brief examination of the contents, pictures and videos were sent from the Samsung Galaxy S3 with the rhickman1989 account to both the DeciphForensics and DecipForensics2 accounts. The same acquisition process was followed again after sending these “snaps.”
All examination took place using AccessData’s Forensic Toolkit version 4.0.2.33.
Snapchat Structure
The majority of Snapchat data is stored within the data/data/com.snapchat.android folder. There are four folders within this directory, with two folders within the cache folder.
Examination of the Samsung Galaxy S3 revealed that within the shared_prefs folder are several XML files: CameraPreviewActivity.xml, com.google.android.gcm.xml, com.snapchat.android_preferences.xml, and SnapPreviewActivity.xml.
The com.snapchat.android_preferences.xml File
This file is where the majority of information stored by Snapchat is located. Within this file is a listing of all the contacts stored on the device. This is done with the permission allowed by the user for the application to read the contacts on the device.
Below the list of contacts is a listing of Snapchat messages. It appears that there is a set of fields stored for each message in Snapchat. The following are the fields stored in this section of the XML file: type, mSender, mWasViewed, mCaptionPosition, mCaptionOrientation, mIsLoading, mIsTimerRunning, mIsBeingViewed, MWasOpened, mWasScreenshotted, mDisplayTime, mId, mTimestamp, mStatus, mIcon, and mMediaType.
We sent only two pictures from the DecipForensics2 account, and one was viewed and expired. Within this XML file are two records that show the mSender field set to “decipforensics2.” Of those two records, one has the mWasOpened set to “true.” The author kept documentation as to which images were opened and allowed to expire and which are not, so it is known which image is tied to this record.
The mTimestamp field is stored in Epoch format. Upon conversion of this value, it showed the time that the image was either taken or viewed. Further research will need to be done to determine which it is, however, the time is within the timeframe of both being sent and viewed. Unfortunately, the author did this within a few minutes of each other and did not record the exact time sent.
The mId field for the picture shown to the left is “270518365528484358r.” The mTimestamp field in the same record is “1365528484358.” After converting the Epoch time format to readable format, the time stamp is for April 9, 2013 11:28:04 MDT. The similarities here will be address further in a later section of this paper
The received_image_snaps Folder
Within this folder were located every image sent to the DeciphForensics account on the Samsung Galaxy S3, including the images that had been viewed and were expired. There were some duplicate images with different names as well, the reason for this is unknown.
Android developers created a way for media files such as graphics to be stored on the phone for application use and function without being put into the Gallery application as an image to be viewed. The way that they did this was with .nomedia files. “If a directory has a file named .nomedia, then the media store will not scan and record the metadata of files in that directory” (Hoog, 2011).
Each of the images within the received_image_snaps folder had a .nomedia extension appended to the end of the file name. For example, the name of the file figure 3 is “h1a81hurcs00h1365528700423.jpg.nomedia”. This was likely done to prevent the images stored within this directory from being placed in the gallery or from being scanned by the media store. AccessData’s Forensic Toolkit recognized the .nomedia extension that was appended to the end of the file name and ignored it, displaying the images.
Correlations between the XML Records and the Image Names
There is a small correlation between records within the com.snapchat.android_preferences.xml file and the name of the image file stored in the received_image_snaps folder.
As shown above, there are three correlations between the name of the image, the mTimestamp value, and the mId value. While this is consistent with this image, it is not always consistent with all images. The section in blue is present in several of the other images, only with different numbers following to separate the image.
Conclusion
The author began this research in an attempt to answer several vital questions about the Snapchat application as it is stored and used on Android devices. The author has concluded that metadata is stored for Snapchat images, as shown by the com.snapchat.android_preferences.xml file, and that it contains metadata about expired “snaps” as well as unexpired “snaps,” and that images that are sent via Snapchat are indeed recoverable, and do not “disappear forever.”
Labels:
child saftey,
cookies,
exploit,
forensic,
Francis Gorman,
hacking,
plain text,
recover,
snapchat,
sniffing,
spam,
wifi
Monday, 8 February 2016
Securing your iot devices
2016 has been named the year that the internet of things (iot) takes hold, with a reported 50 million plus devices sold worldwide to date with everything from smart fridges to smart plugs iot is here to stay. It must be noted however with all of this extra connectivity comes a juicy threat surface for cyber criminals to prey on. The main thing consumers need to remember that if you bough a devices that connects to the internet then you can be guaranteed that it needs to be secured. In this post I am going to outline a number of steps you can take to help protect yourself and your family from becoming victims of a cyber attack.
1) Keep your devices up to date
This goes for all devices that connect to the internet but I would especially recommend it for iot devices as new exploits are exposed manufactures may push down patches to solve the vulnerability and therefor you should regularly check to make sure your device is running the latest software.
2) Change the default password on your device
This is a very important step to take as the majority of iot devices are mass produced with a default login and not changing this on day one will leave yourself vulnerable to attack. May I suggest using a password that is at least 10 character long with special characters and capitals and numbers i.e don't use your last name and type 123 after it.
3) Be familiar with your devices privacy section
What kind of information are you saving or sharing through this device and what guarantees are put in place that this information is been protected. Don't assume just because the manufacturer says its a secure device to use that it is and make sure your information isn't been shared with third parties.
4) Be carefully buying a second hand device or selling your own device
Buying a second hand device on line may come pre-installed with malware or a backdoor only buy second hand devices from a reputable dealer. On the flip side think long and hard about selling your device, resetting a device may look like all your data has been cleared but with a little know how a lot of this information may be retrieved. There are a number of programs out there that ensure proper data erasure and this may be something you should look into first.
Monday, 14 December 2015
Securing your android (the basics)
I have been asked a bit lately about securing android devices as I tend to focus on the apple side of things as I myself use the iPhone. There is a myth out there that android is inherently insecure and this really isn't true, android out of the box is pretty good its the user that make the device insecure. The real issue with android is anyone can make an app and upload it to their store they don't check first to see if you are a potential cyber criminal. I think from memory that at one stage in the past few years the top 5 apps in the android store were in fact trojan horses this might be wrong but I am pretty sure their is some truth their I need to go back and double check this. So to minimize the waffle you ask "what do I need to do to secure my android?" Well I have put together a number of steps that if followed will definitely help you get to a place where you can feel "secure".
1) Do not save all of your passwords in your device! I don't know why I need to say this but people naturally tend to save their passwords for easy access of whatever the reason on their devices. This is a very bad practice and you should avoid this, think of memorizing your passwords of a way to delaying Alzheimer's and not getting ripped off by cyber criminals.
2) Use your devices inbuilt security features, If you are running on Jelly Bean, you can have a screen lock and encryption enabled to further enhance your security. Use these features they will help you keep your device safe.
3) Androids allow you to lock your apps you should use this feature especially for apps that hold sensitive information. Their is a free app that you can download to enable this feature called App Lock.
4) If you are installing an app read what permissions the app want's!!! If you are downloading some recipe app it doesn't need access to your camera, microphone and contacts. This should be common sense but for some reason people download apps and click ok to everything.
5) Download a mobile security app, androids are very much open to virus's and malware in comparison to their i0S counterparts. An app I think is pretty good is avast!mobile security.
6) One of the most important things you can do to secure your android is secure your network. I know you wont listen but try to avoid using public networks. You can protect your information by using apps like Hideninja VPN so that your outgoing connection is always encrypted, making it harder for anyone to sabotage your data. If you suspect that your device is being attacked, WiFi Protector can help fend off these attackers. To further enhance your network security you can apply settings from SecDroid but note that this app is only for rooted phones.
1) Do not save all of your passwords in your device! I don't know why I need to say this but people naturally tend to save their passwords for easy access of whatever the reason on their devices. This is a very bad practice and you should avoid this, think of memorizing your passwords of a way to delaying Alzheimer's and not getting ripped off by cyber criminals.
2) Use your devices inbuilt security features, If you are running on Jelly Bean, you can have a screen lock and encryption enabled to further enhance your security. Use these features they will help you keep your device safe.
3) Androids allow you to lock your apps you should use this feature especially for apps that hold sensitive information. Their is a free app that you can download to enable this feature called App Lock.
4) If you are installing an app read what permissions the app want's!!! If you are downloading some recipe app it doesn't need access to your camera, microphone and contacts. This should be common sense but for some reason people download apps and click ok to everything.
5) Download a mobile security app, androids are very much open to virus's and malware in comparison to their i0S counterparts. An app I think is pretty good is avast!mobile security.
6) One of the most important things you can do to secure your android is secure your network. I know you wont listen but try to avoid using public networks. You can protect your information by using apps like Hideninja VPN so that your outgoing connection is always encrypted, making it harder for anyone to sabotage your data. If you suspect that your device is being attacked, WiFi Protector can help fend off these attackers. To further enhance your network security you can apply settings from SecDroid but note that this app is only for rooted phones.
Labels:
android,
anti virus,
attack,
breaking,
decrypt,
Disable,
exploit,
forensic,
Francis Gorman,
sniffing,
software patched,
spam,
stealing,
vpn,
wifi
Tuesday, 8 December 2015
Protecting Windows 10 (The Basics)
Over the past few months Microsoft have been firing out their new operating system Windows 10 to the world for free. This blog is more aimed at anyone who is just after installing the operating system as chances are if you are a windows user you may have already upgraded or will be doing so in the near future. Like most things that come fresh out of the box to make them work to a level you might expect takes some tweaking. I am going to focus on a few basic steps you should take right away to make your new operating system secure.
1) Run the windows update straight away, I know you may have spend an hour or two installing the dam thing but running windows update will make sure your operating system has the latest patches. To find windows update just click the little search bar at the bottom of your screen and type "windows update" once opened just hit "check for updates" and your done.
2) System restore is turned off by default in Windows 10 so you might want to turn this on. Microsoft have renamed this function as "system protection" so to turn this on head back down to the little search bar and type "This PC" when the logo appears right click on it and select "Properties" click on "system protection" then click "Configure" and turn system protection on.
3) Check your Windows 10 privacy setting by default everything and I mean everything in here is turned on. To get here you go to START > Settings> Privacy spend a bit of time looking over this and make sure you are happy with it.
4) Make sure that all of your applications are updated in an earlier post I mentioned that Secunia PSI was a good application to check this.
5) Make sure you have your anti-virus turned on if you don't have an anti-virus Windows has a build in AV called Windows Defender. You can find Defender by going to the search bar and typing "Windows Defender".
Labels:
.Locky,
android,
Cyber security,
exploit,
Francis Gorman,
hacking,
HTTPS,
iot,
Network based,
plain text,
Prepare against,
protected,
Ransomware,
recover,
software patched,
targeted adverts,
tracking,
wifi,
Windows 10
Saturday, 5 December 2015
Staying anonymous online (The Basics)
This is a topic that seems to keep popping up over and over again for many different reasons some good and some bad. In my opinion everyone should have the right to remain anonymous online if they choose to do so. I know in the extreme cases Governments are claiming that terrorists and criminals are using encryption of a means to carry out organised crime and nation attacks, however does this mean the rest of free society should give up the right to remain anonymous online? If you believe that the answer to this question is no then you can take a number of steps to help keep your online identity non-existent. The steps below in no way mean that the FBI won't know who you are if you start doing some illegal shit like hiring an assassin on the dark-net so I strongly advise against doing so.
1) If you are the type of person who wants no digital footprint then you might not want to join social media sites. The amount of personal data that social networking sites like Facebook, Google Plus and Twitter have harvested from their billions of users is shocking. Head to facebook.com/settings and click ‘Download a copy of your Facebook data’ and you might be surprised to see just how much information is on file. More or less everything you have ever done on Facebook is saved in this file so you can kind of get a feel for just how much information these sites hold on you.
2) My second tip is another rather simple approach, go incognito The top four most popular browsers - Google Chrome, Mozilla Firefox, Internet Explorer and Safari - have a private browsing mod. With private browsing activated, your browser will not store cookies or internet history on your computer. This is quiet a limited function and is really only of use to hide information from others such as a significant other. I say this because Private browsing does not securely hide your identity or browsing activities beyond your local machine as your IP address can still be tracked.
3) It is a known fact that many websites track and monitor their users activity, this can actually cost you money. An example of this is that plane ticket that you want to buy so you regularly check to see if its sold out, then when you have the cash the bloody ticket has gone up in price, the reasons for this could very well be website tracking. The issue with website tracking is you can't see if the websites you are visiting are actually tracking you. Ghostery is a free browser extension - available on all major web browsers - that will reveal these trackers, also known as web bugs. You can then decide which web bugs you’re comfortable with tracking you and which ones you’d like to block.
4) Stop using Dropbox, I know that its a handy tool but as Edward Snowden once stated about Dropbox "they are a cloud service hostile to privacy". Lucky enough if you still want a way to share your files Snowden himself recommends that you use Spideroak to do so. The reason for this being that Spideroak is a zero-knowledge encrypted data backup, share, sync, access and storage service.
5) Use an alternative search engine to the mainstream, I suggested in a previous post that the best search engine for this is DuckDuckGo, which promises never to track your searches and “emphasizes protecting searchers’ privacy and avoiding filter bubble of personalized search results.
6) Reconsider your phone options, if you have a smartphone then staying anonymous just became a whole lot harder. The reason for this is for some reason every app you download these days wants access to your location,contacts,camera,microphone etc which makes staying off the grid impossible really. If you are super parnoid may I suggest investing in the super cool name "Blackphone" This is an ‘NSA-proof’ smartphone that claims to provide privacy features for texts, emails, web browsing and phone calls.
7) Use a Virtual Private Network (VPN)!!! I am sick of repeating this and if you really are serious about staying anonymous online this is simply a must have. You ask what is a VPN? Well essentially it hides your IP address and runs all your online data via a secure and encrypted virtual tunnel, which can keep websites from tracking your online activity or even knowing which country you’re browsing from (which is great for American Netflix). The catch with a using a VPN is don't ever trust a free one so you will need to shell out a few quid every month for the privilege of the service. Their has been a lot of talk recently about how secure certain VPN's are so do some of your own research and find the best one for you.
8) If you are using a popular webmail service such as Gmail then you might want to either change to a more secure provider or else add some security to your current provider. To do this I would suggest installing Mailvelope. Mailvelope is a browser extension for Google Chrome or Mozilla Firefox that brings OpenPGP encryption to your webmail service. Similar extensions exist, such as SecureGmail, which encrypts and decrypts emails you send through Gmail. Alternatively you could start using a webmail service such as Hushmail. Hushmail is currently very popular, it provides a private email account with no ads, built-in encryption and unlimited email aliases. Their is a limited free version of Hushmail however like everything you need to pay to get all the bells and whistles. For the more paranoid their is always the option of Disposable Email Addresses (DEAs). These are anonymous and temporary. They allow users to quickly create new email addresses as-and-when they’re needed, which can then be disposed of after use. There are many companies that provide this type of service however the more reliable one may come in the form of Guerrilla Mail and Mailinator.
6) Reconsider your phone options, if you have a smartphone then staying anonymous just became a whole lot harder. The reason for this is for some reason every app you download these days wants access to your location,contacts,camera,microphone etc which makes staying off the grid impossible really. If you are super parnoid may I suggest investing in the super cool name "Blackphone" This is an ‘NSA-proof’ smartphone that claims to provide privacy features for texts, emails, web browsing and phone calls.
7) Use a Virtual Private Network (VPN)!!! I am sick of repeating this and if you really are serious about staying anonymous online this is simply a must have. You ask what is a VPN? Well essentially it hides your IP address and runs all your online data via a secure and encrypted virtual tunnel, which can keep websites from tracking your online activity or even knowing which country you’re browsing from (which is great for American Netflix). The catch with a using a VPN is don't ever trust a free one so you will need to shell out a few quid every month for the privilege of the service. Their has been a lot of talk recently about how secure certain VPN's are so do some of your own research and find the best one for you.
8) If you are using a popular webmail service such as Gmail then you might want to either change to a more secure provider or else add some security to your current provider. To do this I would suggest installing Mailvelope. Mailvelope is a browser extension for Google Chrome or Mozilla Firefox that brings OpenPGP encryption to your webmail service. Similar extensions exist, such as SecureGmail, which encrypts and decrypts emails you send through Gmail. Alternatively you could start using a webmail service such as Hushmail. Hushmail is currently very popular, it provides a private email account with no ads, built-in encryption and unlimited email aliases. Their is a limited free version of Hushmail however like everything you need to pay to get all the bells and whistles. For the more paranoid their is always the option of Disposable Email Addresses (DEAs). These are anonymous and temporary. They allow users to quickly create new email addresses as-and-when they’re needed, which can then be disposed of after use. There are many companies that provide this type of service however the more reliable one may come in the form of Guerrilla Mail and Mailinator.
Labels:
Dcrypt,
Facebook,
Francis Gorman,
hacking,
spam,
ssl,
tracking,
vpn,
Windows 10
Wednesday, 2 December 2015
Steps to take after the Vtech Hack
In the last week the figures released from toymaker VTech surrounding the massive hack they have suffered is startling. The worst part about this hack is it shows that children are not immune to cyber crime. It is important to first realise the scale of this attack and just how many children have been affected worldwide. Below are statistics detailing how many individuals data has been leaked and in what countries along with if the data was that of an adult or a child. As you can see from the statistics below I have highlighted Ireland, the only reason for this is that I am Irish.
Country Parent Accounts Child Profiles
United States 2,212,863 2,894,091
France 868,650 1,173,497
United Kingdom 560,487 727,155
Germany 390,985 508,806
Canada 237,949 316,482
Others 168,394 223,943
Spain 115,155 138,847
Belgium 102,119 133,179
Netherlands 100,828 124,730
Republic of Ireland 40,244 55,102
Latin America 28,105 36,716
Australia 18,151 23,096
Denmark 4,504 5,547
Luxembourg 4,190 5,014
New Zealand 1,585 2,304
What I find the most frighting about all of this is that a particular VTech service known as Kid Connect was hacked and the information stolen. You may ask why is this frighting and I am going to explain why. Kid Connect is set-up to allow parents and their kids to communicate. That information includes kids head-shots and chat logs between parents and children. Most, if not all, of these cases, the logs, pictures, and recordings can be traced back to specific usernames, allowing anyone in possession of the hacked data to identify the people chatting as well as those in the pictures.
This may lead to a lot more unforeseen problems down the road but as it stands is just a very uncomfortable situation for parents to be in, and yet again starkly highlights the dangers for children in the digital age.
If you have been affected by this attack you might want to know what steps do you need to take now.
Luckily for you its coming up to Christmas so the VTech spin doctors are in full flight trying to somehow roll out reassuring and efficient damage control to save what's left of the companies reputation. In response to the attacks they have posted a very detailed breakdown of all of the events and the VTech response that can be found here. If you just want the main points I have pulled them out and you can find the below.
What kind of information are stored in the database?
Parent account information including name, email address, secret question and answer for password retrieval, IP address, mailing address, download history and encrypted password.
Kids profiles include name, genders and birthdates.
Encrypted Learning Lodge’s contents including, Kid Connect’s profile photos, undelivered Kid Connect messages, bulletin board postings and Learning Lodge content (ebooks, apps, games etc).
Download sales report logs.
Progress logs to track kids games, for parents’ reference.
It does not contain any credit card information. VTech does not process nor store any customer credit card data on the Learning Lodge website. To complete the payment or check-out process of any downloads made on the Learning Lodge website, our customers are directed to a secure, third party payment gateway.
It does not contain any personal identification data (such as ID card numbers, Social Security numbers or driving license numbers).
Was any credit card information stolen?
No, our Learning Lodge website database does not contain any credit card information and VTech does not process or store any customer credit card data on the Learning Lodge website. To complete the payment or check-out process of any downloads made on the Learning Lodge website, our customers are directed to a secure, third party payment gateway.
Why do you need this customer information?
Learning Lodge allows our customers to download apps, learning games, e-books and other educational content to their VTech products. Customers need to set up an account for such transactions. The information is used to identify the customer and track their downloads. As customer safety and privacy are of utmost importance to us, we are making all necessary adjustments to our system security, which will include only storing such information as is required for our customers to download and enjoy our services. All other information will be deleted from our servers.
Is there anything I can do to better protect myself?
Whilst all personal customer passwords are encrypted, even encrypted data can be susceptible to skilled hackers, so we are advising you to immediately change your passwords on any other sites that may use the same email, secret question and answer, and password combination.
What is VTech doing to protect data stored on Kid Connect?
The Kid Connect service has been temporarily suspended. We are reviewing our security protocols and will delete all unsent messages before we restart the service.
How can I change my password or delete my Learning Lodge account and personal data stored on your servers?
No, our Learning Lodge website database does not contain any credit card information and VTech does not process or store any customer credit card data on the Learning Lodge website. To complete the payment or check-out process of any downloads made on the Learning Lodge website, our customers are directed to a secure, third party payment gateway.
Why do you need this customer information?
Learning Lodge allows our customers to download apps, learning games, e-books and other educational content to their VTech products. Customers need to set up an account for such transactions. The information is used to identify the customer and track their downloads. As customer safety and privacy are of utmost importance to us, we are making all necessary adjustments to our system security, which will include only storing such information as is required for our customers to download and enjoy our services. All other information will be deleted from our servers.
Is there anything I can do to better protect myself?
Whilst all personal customer passwords are encrypted, even encrypted data can be susceptible to skilled hackers, so we are advising you to immediately change your passwords on any other sites that may use the same email, secret question and answer, and password combination.
What is VTech doing to protect data stored on Kid Connect?
The Kid Connect service has been temporarily suspended. We are reviewing our security protocols and will delete all unsent messages before we restart the service.
How can I change my password or delete my Learning Lodge account and personal data stored on your servers?
As an precautionary measure, we have temporarily suspended Learning Lodge and Kid Connect service along with a number of other websites to conduct a thorough security assessment and whilst we implement additional security protocols. We will advise our customers of further action when the websites are ready to be reactivated.
When can we expect that Learning Lodge will be online again? Should I then register again?
We are working as fast as possible to resume our service. We will advise our customers of further action when the websites are ready to be reactivated.
Is it safe for my kids to play with the toys with Learning Lodge app? Could the hacker reach my kids through the devices, trace their activity or location?
Our investigation to date suggests the breach is on the server, not on the device itself. There is no evidence to suggest the toys are not safe at this time. We will continue to investigate and share more information as it becomes available.
Has there been any customer data found leaked on the internet?
We have no evidence that any of the data has been used or distributed criminally. Whilst all personal customer passwords are encrypted, even encrypted data can be susceptible to skilled hackers, so we are advising you to immediately change your passwords on any other sites that may use the same email, secret question and answer, and password combination.
Subscribe to:
Posts (Atom)