After dealing with a number of nasty .Locky ransomware cases in the past few weeks I am delighted to announce that Bitdefender has created an anti-ransomware vaccine that blocks the strains CTB-Locker, Locky and TeslaCrypt. This is something that everyone should be downloading ASAP and trust me on this as prevention in this case is much better than paying the fine.
According to data recently published by Fortinet, top ransomware
families are CryptoWall, Locky, and TeslaCrypt, while Cryptowall is
predominant, Lock is rapidly spreading.

The Bitdefender Anti-Ransomware toolkit was developed by the company
years ago to help victims of crypto-ransomware to prevent infections. Some ransomware-decryptors try to exploit encryption flaws in the
ransomware implementation to decrypt files or use encryption keys
discovered by law enforcement during their activity. These conditions are not easy to match, so Bitdefender is promoting
the prevention instead by spreading its anti-ransomware
vaccine. So that is enough of me waffling go and download and install the
anti- ransomware vaccine HERE.
RANSOMWARE DECRYPTOR:
In the case that you have been hit with ransomware there is still the possibility that you will be able to decrypt the encryption depending on the strain.
The National High Tech Crime Unit (NHTCU) of
the Netherlands’ police, the Netherlands’ National Prosecutors Office
and Kaspersky Lab, have been working together to fight the CoinVault and Bitcryptor ransomware campaigns. In doing so they have released a new decryption application that will automatically decrypt all files for Coinvault and Bitcryptor victims. For more information please see this how-to guide. For TelsaCrypt Cisco have also released a decryption tool however I have not personally used this so I can't comment but if you want to take a look you can find it here.
How to Protect Yourself from Macro-based Malware?
Below is a number of pointer's from
The Hacker News on protecting against macro-based malware that may also be of interest.
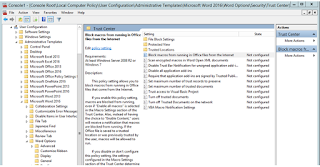
Step 1: Configure Trusted Location
Since disabling Macros is not a feasible option, especially in an office
environment where Macros are designed to simplify the complex task with
automation.
So, if your organization relies on Macros, you can move files that use
Macros into the company’s DMZ (Demilitarized Zone), also called Trusted
Location.
To configure the trusted location, you can navigate via:
User Configuration/Administrative Templates/Microsoft Office XXX
20XX/Application Settings/Security/Trust Center/Trusted Locations
Once configured, the Macros that does not belong to the trusted location
would not run in any way, beefing up your system’s security.
Step 2: Block Macros in Office Files that came from the Internet
Microsoft had
recently unveiled
a novel method by implementing a new tactical security feature to limit
the Macro execution attack in MS Office 2016, ultimately preventing
your system from hijacking.
The new feature is a group policy setting that lets enterprise
administrators to disable macros from running in Office files that come
from the Internet.
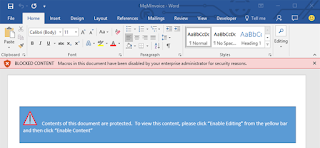
The new setting is called, "
Block macros from running in Office files from the Internet" and can be navigated through the group policy management editor under:
User configuration > Administrative templates > Microsoft Word 2016 > Word Options > Security > Trust Center
It can be configured for each Office application.
By enabling this option, macros that come from the Internet are blocked
from running even if you have 'enable all macros' in the Macros
Settings.
Moreover, instead of having the option to '
Enable Editing,' you'll receive a notification that macros are blocked from running, as the document comes from an Untrusted Source.
The only way to run that particular Office file is to save it to a trusted location, allowing macros to run.